🛡️ How to Set Up a Secure Remote Work Environment for Your Team
Why Security Can’t Be an Afterthought in Remote Work
The shift to remote work has unlocked flexibility and global talent, but it has also exposed businesses to a wide range of cybersecurity threats. From unsecured Wi-Fi to phishing scams and data leaks, remote teams are now frontline targets.
At VertexPro, we help businesses adapt to this reality with secure, scalable, and easy-to-manage remote infrastructure. In this guide, we’ll walk you through everything you need to create a remote work environment that’s productive and protected against cyber risks.
⸻
🔍 Understanding the Risks of Remote Work
Before you build the solution, you need to understand the threats. Some of the most common vulnerabilities in remote work include:
• ❌ Using personal or outdated devices without proper protection
• ❌ Public or unsecured home Wi-Fi networks
• ❌ Lack of centralized IT visibility or control
• ❌ Poor password practices and lack of MFA
• ❌ Increased risk of phishing and social engineering attacks
Any of these gaps can be exploited to access company data or disrupt operations.
⸻
✅ Step-by-Step: Setting Up a Secure Remote Work Environment
Let’s break down how to build a secure digital workspace that enables productivity without compromising security.
⸻
1. 🖥️ Enforce Device & Endpoint Security
Every device that connects to your business network is a potential attack vector.
What to do:
• Require company-managed laptops or enforce MDM (Mobile Device Management)
• Install antivirus, firewall, and endpoint detection software (e.g., CrowdStrike, SentinelOne)
• Keep operating systems and apps up to date with automated patching
⸻
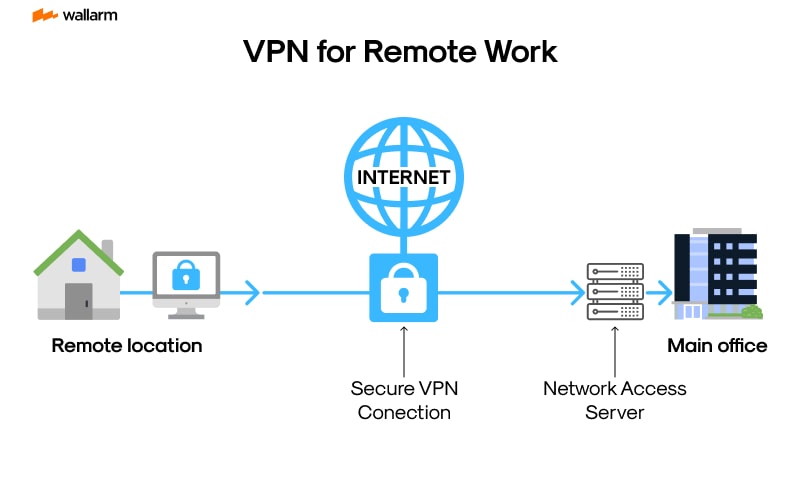
2. 🌐 Secure Access with VPN & Zero Trust
Remote workers should never connect to sensitive systems via open networks.
What to do:
• Set up a reliable, encrypted VPN with split tunneling
• Implement a Zero Trust Architecture — verify every user and device, every time
• Use IP whitelisting and geofencing for sensitive applications
⸻
3. 🔑 Enforce Strong Identity and Access Management
Control who gets access to what, and how.
What to do:
• Use Single Sign-On (SSO) to centralize user authentication
• Enforce Multi-Factor Authentication (MFA) across all services
• Apply the Principle of Least Privilege — limit access to only what is necessary
⸻
4. ☁️ Use Secure Cloud Collaboration Tools
Email and file sharing are major threat surfaces. Make sure they’re protected.
What to do:
• Use secure collaboration tools like Google Workspace, Microsoft 365, or Notion
• Enable data loss prevention (DLP) policies for file sharing
• Regularly audit permissions on cloud drives and shared folders
⸻
5. 👨🏫 Train Your Team on Cyber Hygiene
Your security is only as strong as your least informed employee.
What to do:
• Offer ongoing cybersecurity training (phishing, password hygiene, etc.)
• Conduct simulated phishing campaigns
• Create an easy way for employees to report suspicious activity
⸻
6. 📊 Monitor and Respond in Real-Time
You need visibility into everything that’s happening across your remote workforce.
What to do:
• Deploy a Security Information & Event Management (SIEM) platform
• Use behavior analytics to detect anomalies
• Set up automated alerts for unauthorized access attempts
⸻
7. 🧩 Backups and Incident Response
Assume something will eventually go wrong — be prepared.
What to do:
• Implement automatic, encrypted backups of key data (daily or real-time)
• Store backups in separate physical/cloud locations
• Develop and rehearse a remote incident response plan
⸻
📈 Tools We Recommend at VertexPro
Here are some of our favorite tools to secure remote teams:
Category Tools
VPN NordLayer, Perimeter 81
Endpoint Security CrowdStrike, Bitdefender GravityZone
MDM Jamf, Microsoft Intune
Collaboration Google Workspace, Microsoft Teams
Password Management 1Password, Bitwarden
Monitoring Splunk, Datadog, Wazuh
⸻
💼 Why Choose VertexPro?
We’ve helped startups, SMBs, and enterprise teams transition from chaotic remote setups to secure, compliant, and high-performance work environments. With us, you don’t just get recommendations — you get implementation, monitoring, and peace of mind.
Whether you’re a tech company scaling up, or a financial firm seeking regulatory compliance, we tailor every setup to your industry and risk profile.
⸻
📞 Ready to Upgrade Your Remote Work Security?
Let’s secure your workforce — wherever they are.
👉 Book a free consultation
👉 Or explore our Managed Security Services at vertexpro.io